5. Microsoft Defender for Office (MDO)
-
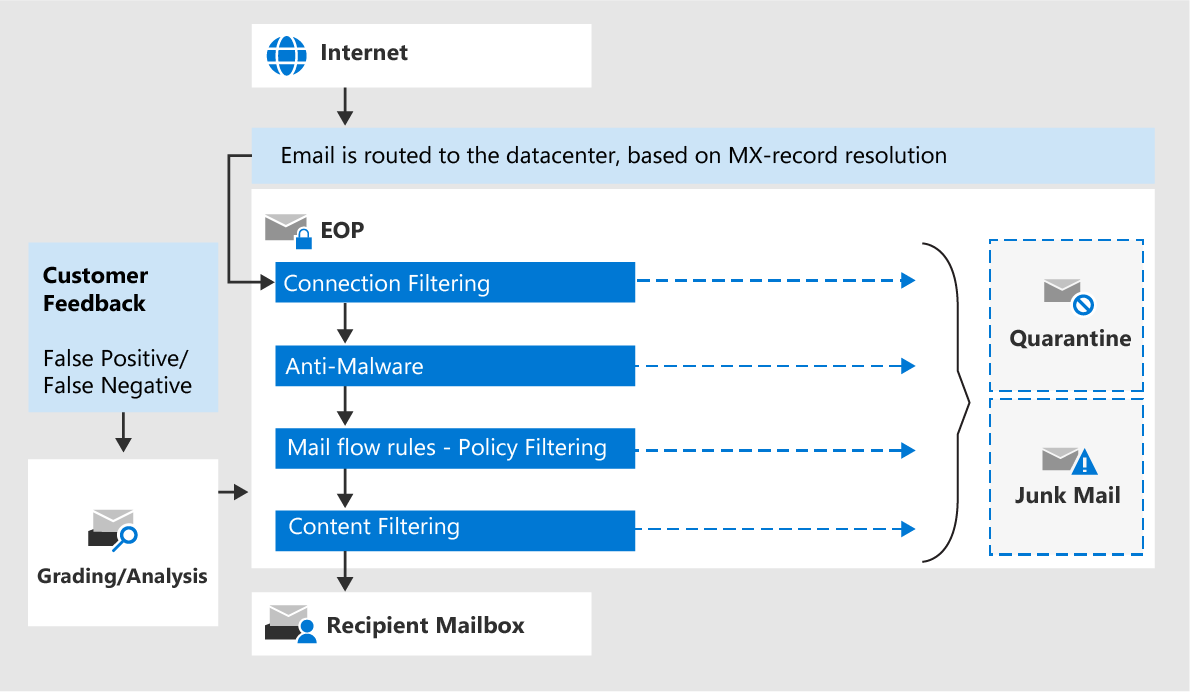
Understand how EOP works: https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/eop-about?view=o365-worldwide#how-eop-works
-
Order and precedence of email protection https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/how-policies-and-protections-are-combined?view=o365-worldwide
-
Appendix - It's important to understand how user allows and blocks, tenant allows and blocks, and filtering stack verdicts in EOP and Defender for Office 365 complement or contradict each other. https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/how-policies-and-protections-are-combined?view=o365-worldwide#appendix
Recent BEC activity (Business Email Compromise) https://x.com/jhencinski/status/1616543412940931075?s=61&t=C1HAZW3QfTIcWUDtZNoHOw
Great NEW update on Automation https://www.techrepublic.com/article/microsoft-defender-365-automation-fight-automated-attacks/
Ways of working
- Top 20 most-viewed admin help articles this month https://learn.microsoft.com/en-us/microsoft-365/admin/top-m365-admin-articles?view=o365-worldwide
- How to secure your business data with Microsoft 365 for business https://learn.microsoft.com/en-us/microsoft-365/admin/security-and-compliance/secure-your-business-data?view=o365-worldwide
- Basic authentication sign-in prompts are blocked by default in Microsoft 365 Apps https://learn.microsoft.com/en-us/deployoffice/security/basic-authentication-prompts-blocked
Enable Telemetry
-
Step-by-Step guide https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/step-by-step-guides/step-by-step-guide-overview
-
Try in Audit mode https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/try-microsoft-defender-for-office-365
-
Enhanced Filters aka Skip Listing (use for Migration) https://learn.microsoft.com/en-us/Exchange/mail-flow-best-practices/use-connectors-to-configure-mail-flow/enhanced-filtering-for-connectors Especially this last one on Enhanced Filters, this is where it is possible to enable MDO to co-exist with what ever 3rd party system you are using today, but it will typically require an MX record change, and is not an undertaking to be taken lightly. The main point - it is possible to have co-existense - but this should NOT be seen as a long term process!!
-
Data retention information for Microsoft Defender for Office 365 https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/mdo-data-retention?view=o365-worldwide
Validate and Test
- AIR - make sure you Enable this https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/office-365-air
-
How AIR works https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/office-365-air
-
Integrate Microsoft Defender for Endpoint with Microsoft Defender for Cloud Apps https://learn.microsoft.com/en-us/defender-cloud-apps/mde-integration
Enable Reporting
-
Protect against Threats https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/protect-against-threats
-
What is ZAP? Zero-hour auto purge (ZAP) in Exchange Online https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/zero-hour-auto-purge?view=o365-worldwide
-
Alert Policies in Microsoft 365 https://learn.microsoft.com/en-us/microsoft-365/compliance/alert-policies?view=o365-worldwide
-
Manage mailbox auditing https://learn.microsoft.com/en-us/microsoft-365/compliance/audit-mailboxes?view=o365-worldwide
-
Audit log activities https://learn.microsoft.com/en-us/microsoft-365/compliance/audit-log-activities?view=o365-worldwide
-
View dashboards and reports in the Microsoft 365 Defender portal https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/tenant-wide-setup-for-increased-security?view=o365-worldwide#view-dashboards-and-reports-in-the-microsoft-365-defender-portal
Review and Improve as needed
-
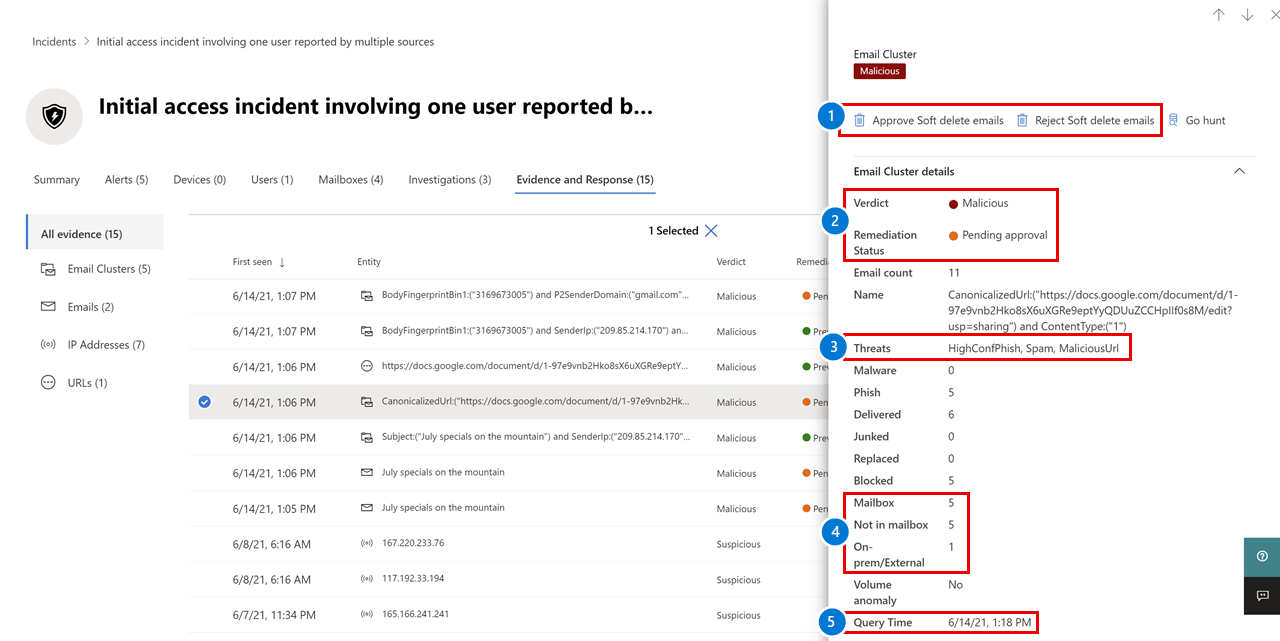
The display of incident evidence for email and email clusters https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/email-analysis-investigations?view=o365-worldwide#the-display-of-incident-evidence-for-email-and-email-clusters
-
Tune anti-phishing protection https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/anti-phishing-protection-tuning?view=o365-worldwide
-
Review and manage remediation actions in Office 365 https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/air-review-approve-pending-completed-actions?view=o365-worldwide
-
Detect & Address compromised user accounts with automated investigation and response https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/address-compromised-users-quickly?view=o365-worldwide
-
Detect and Remediate Illicit Consent Grants https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/detect-and-remediate-illicit-consent-grants?view=o365-worldwide
-
Detect & Respond to a compromised connector https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/connectors-detect-respond-to-compromise?view=o365-worldwide
-
Config Analyzer https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/configuration-analyzer-for-security-policies
-
Recommended Settings https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/recommended-settings-for-eop-and-office365
-
SecOps Guide https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/mdo-sec-ops-guide
-
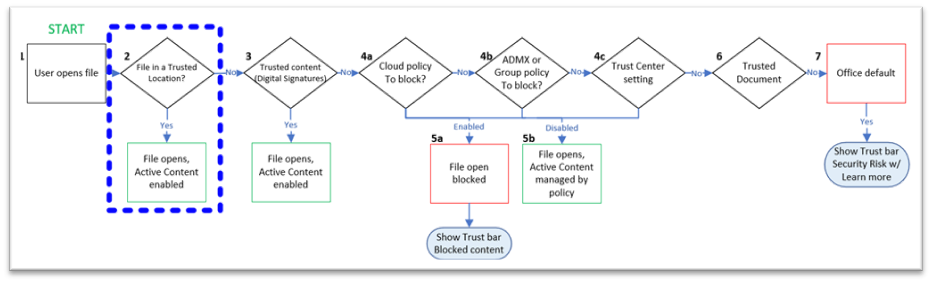
Macros from the internet will be blocked by default in Office https://learn.microsoft.com/en-us/deployoffice/security/internet-macros-blocked
-
Trusted Locations for Office files https://learn.microsoft.com/en-us/deployoffice/security/trusted-locations
Troubleshooting
-
Troubleshooting mail sent to Microsoft 365 https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/mail-flow-troubleshooting?view=o365-worldwide
-
Roles and role groups in Microsoft Defender for Office 365 and Microsoft Purview compliance https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/scc-permissions?view=o365-worldwide
-
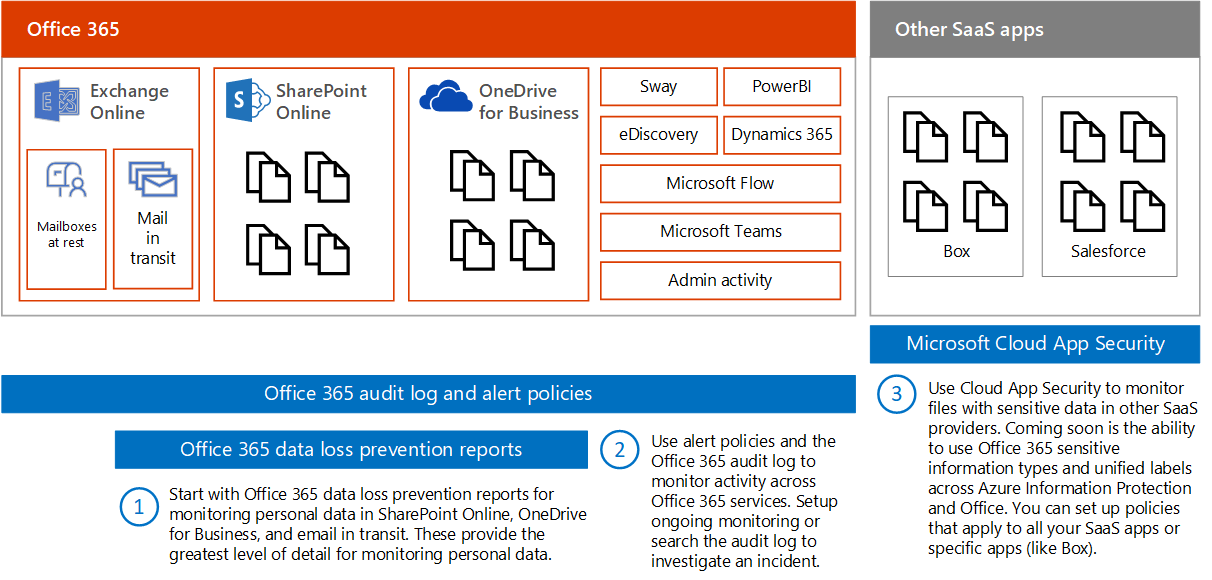
Monitor for leaks of personal data https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/monitor-for-leaks-of-personal-data?view=o365-worldwide
-
Privileged Identity Management (PIM) and why to use it with Microsoft Defender for Office 365 https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/use-privileged-identity-management-in-defender-for-office-365?view=o365-worldwide
-
Add support for anonymous inbound email over IPv6 in Microsoft 365 https://learn.microsoft.com/en-us/microsoft-365/security/office-365-security/mail-flow-inbound-ipv6-support-about?view=o365-worldwide