9. ASD/ACSC Essential 8 & Hardening Guides
ASD Essential 8 (now ACSC)
-
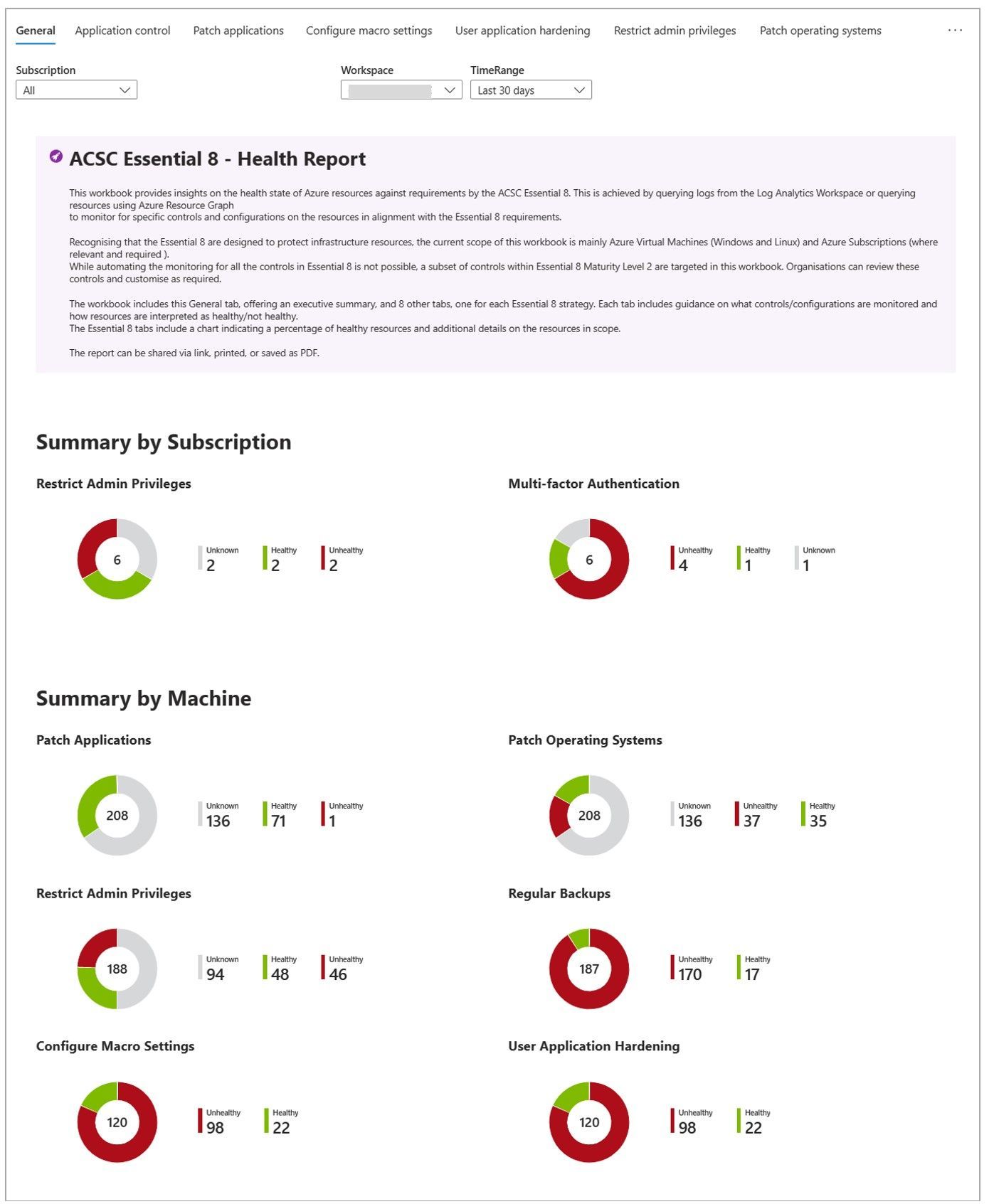
Please start with this - ACSC Essential 8 – Health Report in Microsoft Sentinel https://techcommunity.microsoft.com/t5/microsoft-sentinel-blog/acsc-essential-8-health-report-in-microsoft-sentinel/ba-p/3755702
-
Great high level on all Essential 8 https://aka.ms/e8guides
- Collection of Australian M365 content on Essential 8 https://m365maps.com/australia.htm
- Microsoft Cybersecurity Reference Architecture https://aka.ms/MCRA or https://learn.microsoft.com/en-us/security/cybersecurity-reference-architecture/mcra
- General on Essential 8 https://learn.microsoft.com/en-us/compliance/anz/e8-overview
- Daily backups https://learn.microsoft.com/en-us/compliance/anz/e8-backups
- Australian IRAP https://learn.microsoft.com/en-us/azure/compliance/offerings/offering-australia-irap & https://servicetrust.microsoft.com/Viewpage/AustraliaIRAP
- Implmenting Essential 8 with Microsoft tooling

Local Australian E8 Guides
-
Microsoft Service Trust Portal has the local Essential 8 guides https://aka.ms/e8guides here you will find the documentations covering the following specifics (dated Aug 2023)
-
Microsoft General - Essential Eight - Config Macros
- Microsoft General - Essential Eight - User Application Hardening
- Microsoft General - Essential Eight - Restricting Admin Priv
- Microsoft General - Essential Eight - Patch OS
- Microsoft General - Essential Eight - Backup
- Microsoft General - Essential Eight - Patch Applications
- Microsoft General - Essential Eight - MFA
Hardening Guidance from ACSC
-
For Windows 10 21H1 https://www.cyber.gov.au/acsc/view-all-content/publications/hardening-microsoft-windows-10-version-21h1-workstations
-
For Macro's
- Restricting Microsoft Office Macros https://www.cyber.gov.au/resources-business-and-government/maintaining-devices-and-systems/system-hardening-and-administration/system-hardening/restricting-microsoft-office-macros &
-
Technical example: Configure macro settings https://www.cyber.gov.au/resources-business-and-government/essential-cyber-security/small-business-cyber-security/small-business-cloud-security-guide/technical-example-configure-macro-settings
-
For Intune https://github.com/microsoft/Intune-ACSC-Windows-Hardening-Guidelines
- WDAC Policy creation from DTA https://desktop.gov.au/blueprint/abac/wdac-policy-creation.html
AD onPrem
A list of resources from DART perspective on Active Directory - courtesy of Matt Zorich (X @reprise99)
- BloodHound Edges https://bloodhound.readthedocs.io/en/latest/data-analysis/edges.html
- AD Security https://adsecurity.org/?page_id=4031
- iRed Team notes https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse...
- SID History Persistence https://adsecurity.org/?p=1772
- How AdminSdHolder & SDProp work https://techcommunity.microsoft.com/t5/ask-the-directory-services-team/five-common-questions-about-adminsdholder-and-sdprop/ba-p/396293...
- Recovering from systemic identity compromise https://learn.microsoft.com/en-us/azure/security/fundamentals/recover-from-identity-compromise
- Abusing Active Directory ACLs/ACEs https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/acl-persistence-abuse...
- Defender for Identity Alerts Overview https://learn.microsoft.com/en-us/defender-for-identity/alerts-overview...
- Best practices for securing AD https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/plan/security-best-practices/best-practices-for-securing-active-directory
- Mimikatz DCSync Abuse https://adsecurity.org/?p=1729
- Kerberoasting Overview https://ired.team/offensive-security-experiments/active-directory-kerberos-abuse/t1208-kerberoasting...
- Monitoring AD for signs of compromise https://learn.microsoft.com/en-us/windows-server/identity/ad-ds/plan/security-best-practices/monitoring-active-directory-for-signs-of-compromise
Exchange Permissions check
These two are subtly different, the first is on mailboxes, the second is more focused on the Outlook Folders
- https://office365itpros.com/2020/03/16/exchange-online-mailbox-permissions/
- https://github.com/12Knocksinna/Office365itpros/blob/master/ReportMailboxPermissionsMailboxes.PS1
- https://office365itpros.com/2020/03/23/reporting-exchange-online-folder-permissions/
- https://github.com/12Knocksinna/Office365itpros/blob/master/ReportPermissionsFolderLevel.PS1